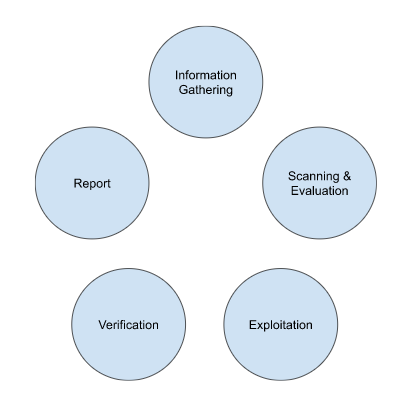
The frequency of pentesting depends on the specific needs and risk profile of the organisation. Here are some factors to consider when determining the frequency of pentest:
- Sensitivity of data
- Network complexity
- Regulatory requirements
- Change management
In general, it is a good idea to conduct at least one pentest per year, although more frequent testing may be necessary depending on the organisation’s risk profile and the sensitivity of it’d data. It is also a good idea to conduct a pentest whenever there is a significant change to the organisation’s systems or network